前一阵偶然看到google 提醒大家在10月前给自家站点启用https的新闻,正好时间也差不多到了,这2天也有空,于是做了1次尝试。
首先看证书,2010年也折腾过免费StartSSL证书,还挺复杂,而且StartSSL据说2016年出事了。
还好现在有了 Let’s Encrypt,还有自动化部署工具certbothttps://certbot.eff.org/,简直是太轻松了:)
我这台服务器环境是centos7+nginx, 命令如下https://certbot.eff.org/#centosrhel7-nginx,其他环境更加智能
$ yum -y install yum-utils
$ yum-config-manager --enable rhui-REGION-rhel-server-extras rhui-REGION-rhel-server-optional
$ yum install certbot-nginx
$ certbot --nginx
几乎就要秒搞定了,结果环境不一样,卡了几个地方,如下
certbot --nginx
提示
certbot nginx: [emerg] open() "/etc/nginx/nginx.conf" failed
可以大概猜到,其实是nginx.conf不是常规的目录,certbot命令找不到路径,但是具体要带什么参数,这一步卡住了,于是goole,找到了下面的命令
certbot --nginx --nginx-server-root /usr/local/nginx/conf
执行有效 ,按提示,输入邮箱,同意协议,启用服务器上的站点。
类似过程如下
[root@Nvps ~]# certbot --nginx --nginx-server-root /usr/local/nginx/conf
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel):[email protected]
Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org
-------------------------------------------------------------------------------
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.1.1-August-1-2016.pdf. You must agree
in order to register with the ACME server at
https://acme-v01.api.letsencrypt.org/directory
-------------------------------------------------------------------------------
(A)gree/(C)ancel: A
-------------------------------------------------------------------------------
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about EFF and
our work to encrypt the web, protect its users and defend digital rights.
-------------------------------------------------------------------------------
(Y)es/(N)o: Y
Starting new HTTPS connection (1): supporters.eff.org
Which names would you like to activate HTTPS for?
-------------------------------------------------------------------------------
1: wanjie.info
2: blog.wanjie.info
3: www.wanjie.info
-------------------------------------------------------------------------------
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel):1 2 3
Obtaining a new certificate
Resetting dropped connection: acme-v01.api.letsencrypt.org
Performing the following challenges:
tls-sni-01 challenge for wanjie.info
tls-sni-01 challenge for blog.wanjie.info
tls-sni-01 challenge for www.wanjie.info
Waiting for verification...
Cleaning up challenges
Failed authorization procedure. wanjie.info (tls-sni-01): urn:acme:error:tls :: The server experienced a TLS error during domain verification :: remote error: tls: handshake failure, www.wanjie.info (tls-sni-01): urn:acme:error:tls :: The server experienced a TLS error during domain verification :: remote error: tls: handshake failure, blog.wanjie.info (tls-sni-01): urn:acme:error:tls :: The server experienced a TLS error during domain verification :: remote error: tls: handshake failure
IMPORTANT NOTES:
- The following errors were reported by the server:
Domain: wanjie.info
Type: tls
Detail: remote error: tls: handshake failure
Domain: www.wanjie.info
Type: tls
Detail: remote error: tls: handshake failure
Domain: blog.wanjie.info
Type: tls
Detail: remote error: tls: handshake failure
To fix these errors, please make sure that your domain name was
entered correctly and the DNS A record(s) for that domain
contain(s) the right IP address. Additionally, please check that
you have an up-to-date TLS configuration that allows the server to
communicate with the Certbot client.
遇到又1个错误
To fix these errors, please make sure that your domain name was
entered correctly and the DNS A record(s) for that domain
contain(s) the right IP address.
查了一下,原来是使用了cloudflare cdn的关系,临时暂停站点,再次执行
certbot --nginx --nginx-server-root /usr/local/nginx/conf
即可。
过程提示如下
[root@Nvps ~]# certbot --nginx --nginx-server-root /usr/local/nginx/conf
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Starting new HTTPS connection (1): acme-v01.api.letsencrypt.org
Which names would you like to activate HTTPS for?
-------------------------------------------------------------------------------
1: wanjie.info
2: blog.wanjie.info
3: www.wanjie.info
-------------------------------------------------------------------------------
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel):1 2 3
Obtaining a new certificate
Performing the following challenges:
tls-sni-01 challenge for wanjie.info
tls-sni-01 challenge for blog.wanjie.info
tls-sni-01 challenge for www.wanjie.info
Waiting for verification...
Cleaning up challenges
Deployed Certificate to VirtualHost /usr/local/nginx/conf/nginx.conf for set(['www.wanjie.info', 'wanjie.info'])
Deployed Certificate to VirtualHost /usr/local/nginx/conf/vhost/blog.wanjie.info.conf for set(['blog.wanjie.info'])
Deployed Certificate to VirtualHost /usr/local/nginx/conf/nginx.conf for set(['www.wanjie.info', 'wanjie.info'])
Please choose whether HTTPS access is required or optional.
-------------------------------------------------------------------------------
1: Easy - Allow both HTTP and HTTPS access to these sites
2: Secure - Make all requests redirect to secure HTTPS access
-------------------------------------------------------------------------------
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
-------------------------------------------------------------------------------
Congratulations! You have successfully enabled https://wanjie.info,
https://blog.wanjie.info, and https://www.wanjie.info
You should test your configuration at:
https://www.ssllabs.com/ssltest/analyze.html?d=wanjie.info
https://www.ssllabs.com/ssltest/analyze.html?d=blog.wanjie.info
https://www.ssllabs.com/ssltest/analyze.html?d=www.wanjie.info
-------------------------------------------------------------------------------
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at
/etc/letsencrypt/live/wanjie.info/fullchain.pem. Your cert will
expire on 2017-12-05. To obtain a new or tweaked version of this
certificate in the future, simply run certbot again with the
"certonly" option. To non-interactively renew *all* of your
certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
成功了,https站点启用完成。
然后,下一步做啥,自然是跑个分咯,用ssllabs检查一下效果????
This server supports weak Diffie-Hellman (DH) key exchange parameters. Grade capped to B.
总分给了一个B,还要改进key 的参数吧,任务继续。
找到这篇文章
https://www.404forest.com/2017/05/08/get-aplus-score-in-ssllabs-with-nginx-and-letsencrypt/
生成健壮的2048位 DH 组:
openssl dhparam -out /etc/ssl/certs/dhparam.pem 2048
然后加入http 板块
ssl_ciphers 'ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA:!DES-CBC3-SHA';
ssl_prefer_server_ciphers on; # use TLSv1 handshake ,pefer server conf
ssl_dhparam /etc/ssl/certs/dhparam.pem;
启用长 HSTS
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains;preload" always;
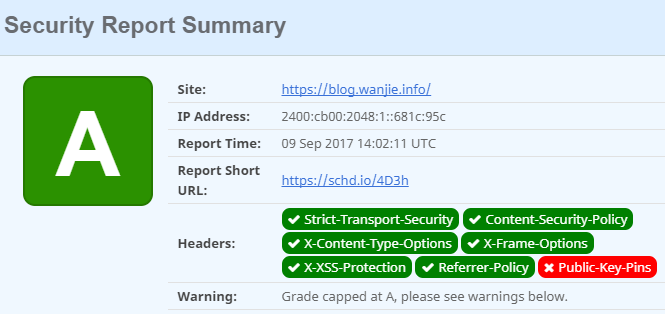
然后根据提示,依次解决 下面的问题,最终打分为A,当然还留了一个实现A+的机会,有空继续折腾
add_header Content-Security-Policy "default-src 'self'; script-src 'self' 'unsafe-inline' 'unsafe-eval' https://ssl.google-analytics.com ; img-src 'self' https://ssl.google-analytics.com https://farm3.staticflickr.com/ https://farm6.staticflickr.com/ http://7jpps1.com1.z0.glb.clouddn.com; style-src 'self' 'unsafe-inline' https://fonts.googleapis.com http://7jpps1.com1.z0.glb.clouddn.com; font-src 'self' https://fonts.googleapis.com https://themes.googleusercontent.com; frame-src https://blog.wanjie.info; object-src 'none'";
add_header X-Content-Type-Options nosniff;
add_header x-frame-options SAMEORIGIN;
add_header X-XSS-Protection "1; mode=block";
add_header Referrer-Policy strict-origin-when-cross-origin;
https://schd.io/4D3h 打分地址
文章评论